Research
In our understanding, Software Engineering is the art of designing useful software products in an efficient way. More precisely, we see “build the right software” and “build the software right” as overarching themes in our research.
Building the software right means designing a software product to be as "helpful" as possible to its users. One aspect of this is – of course – requirements engineering. However, this definition falls far too short. "The right sofware" further addresses issues of interacting with the system, explaining the system to the user (so that the user can build trust in the system), and organizational issues such as involving users in the design, transition, and decision-making processes. To achieve this, software engineers, product owners, AI experts and users must find new ways of working together as a team, far beyond the current scope of agile processes.
Building the software right means developing a software product so that it is of the highest quality. At best 100% guaranteed fault free. Standard approaches such as testing or code reviews can undoubtedly improve software quality. However, these methods can only be applied in domains of low criticality. In critical systems such as aerospace or even real-time financial systems, errors must not occur under any circumstances. To achieve this, efficient combinations of automated and human quality assurance mechanisms must be installed. The vision is for human and AI-powered quality assessors to work hand-in-hand as a team.
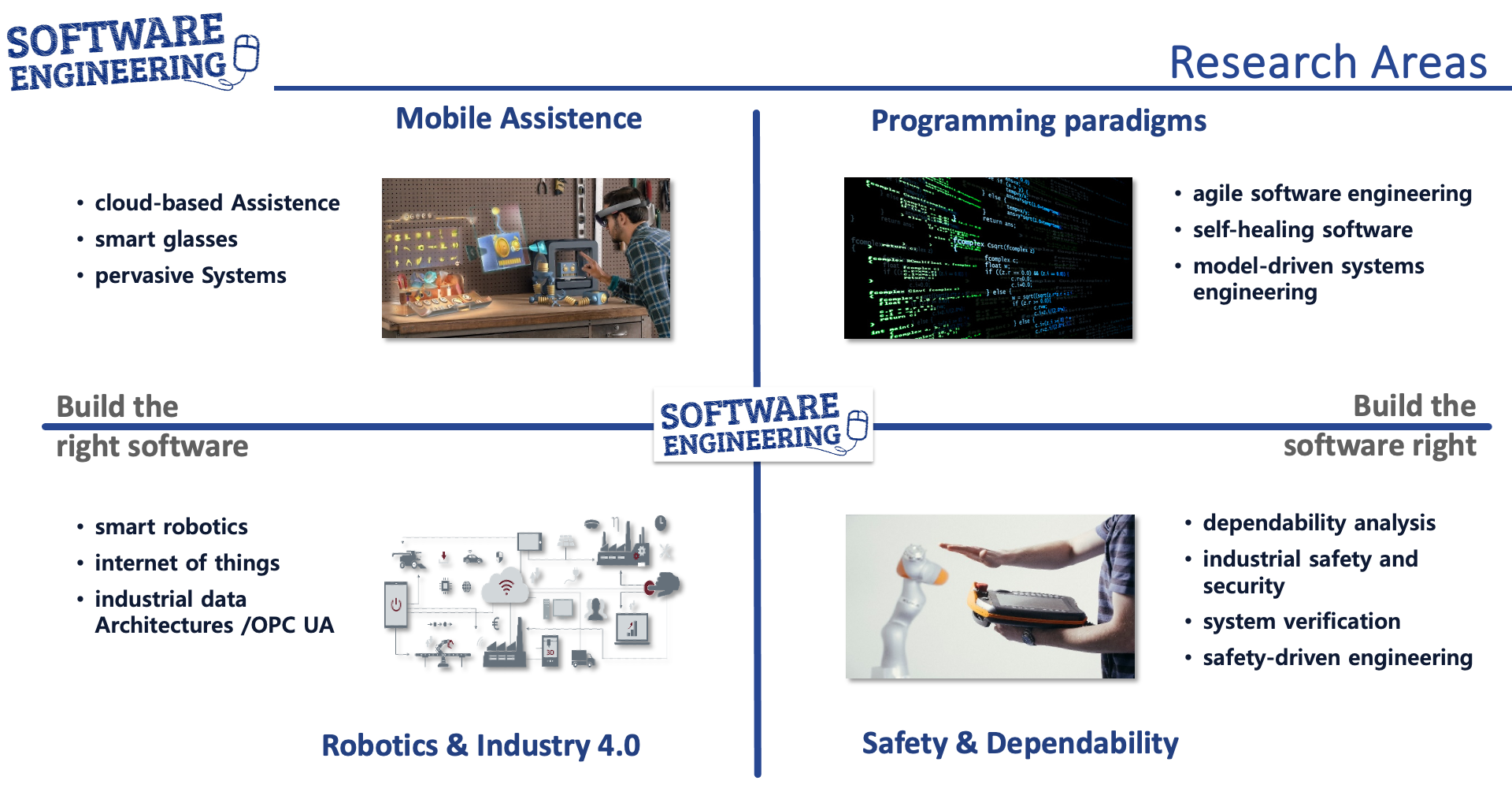
Current Areas of Research
Build the right software - Pervasive Assistance
In the 2000s, mobile phones and data communication lead to a fully connected world. Information became omnipresent. As a consequence, dozends of smart assistant systems emerged helping us in our daily lives. Since the mid 2010s, a new generation of mobile device became popular: wearables. In contrast to mobile phones, these small devices are typically equipped with a limited set of sensors and thus allow to capture some idea of their user’s contexts. However, they have almost no way of communicating pervasively with the user. The second half of the 2020s will very likely be dominated by various types of smart glasses. These gadgets will for the first time allow for truly pervasive assistants. Equipped with smart cameras, they can both capture the interesting part of a users context as well as providing information pervasively – by projecting it directly in the users points of view. Combined, this will reshape our day to day processes as much as the introduction of efficient search and index technology in the web.
In our current research, we focus on design and evaluating such assistance systems methodologically.
Build the software right - AI-supported Programming
AI currently has a huge renaissance. This is mostly due to the breakthroughs in modern parallel computing hardware and GPUs. This allows for efficient training and evaluation of huge neural networks. Such networks have proven to be by far more efficient than any rule-based approach for complex sensory task like image recognition. In recent years, the approaches have been successfully transferred to many parts of private life and work processes.
In our current research, we focus on applying AI-based methods in software development in order to make it more efficient and less error-prone.
Build the software right - Dependable Software
Software allows for many incredible and new functionalities. However, our current software quality assurance processes mostly focus on pure IT systems. For software in technical systems two major problems exist. On the one hand, it is only to some limited extent possible to develop the software incrementally in an agile way (for example a thrust control in an airplane can not be deployed incrementally). Secondly, and maybe even more important, testing alone is neither practical nor sufficient for showing correctness of the software. So new approaches to design, analyse and verify such software systems are needed.
In our current research, we focus on how systems engineering, software engineering and safety engineering can be combined such that an effective combination of human and computer-based quality assurance can be achieved. A particular focus is the intuitive application of formal methods and the evaluation of AI-based functions.
Build the right software - Human-centric programming of robots
Robots are by far the most flexible machines mankind has ever designed. However, currently robots are almost exclusively used in large batch series in industry. The main reason is our current understanding of production automation. The current paradigm follows the mantra “analyse once – find optimal solution – derive optimal process – follow this process”. This mantra is the basis for today’s very high production efficiency. On the other hand, it is also the basis for today’s throw-away-society. Following this mantra, we can only automate fixed processes. As a consequence, underspecified tasks or flexible problems (like repair) can not be automated. We believe the time is ripe to fundamentally change this and design robots such that can flexibly adapt to tasks and ultimately team up with human co-workers. We call this productive teaming.
In our current research, we focus on how to make programing robots more easy or even generate programs automatically as well as designing concepts to measure how robots can prove their human co-workers that they are “trust-worthy”.